Security Update 2016-001 El Capitan…
Unleashing the Power of Nmap: A Comprehensive Guide.
Unleashing the Power of Nmap
Nmap, short for Network Mapper, is a powerful and versatile network scanning tool that has become a staple in the arsenal of many security professionals and network administrators. This article will provide a detailed overview of Nmap, highlighting its features, explaining its usage, and showcasing real-world examples with accompanying pictures.

1. Understanding Nmap
Nmap is an open-source utility used for network exploration and security auditing. It allows you to discover hosts, services, operating systems, and vulnerabilities within a network. Nmap utilizes various scanning techniques, including TCP, UDP, SYN, and ICMP scans, to gather information about target systems.
2. Installation and Basic Usage
To begin, you need to install Nmap on your system, which is available for Windows, macOS, and Linux. Once installed, you can run Nmap from the command line interface. The basic syntax for scanning a target is as follows:
nmap [scan type] [options] [target]
3. Common Scan Types
- TCP Connect Scan
- SYN Scan
- UDP Scan
- OS Detection
4. Advanced Nmap Techniques
- Service and Version Detection
- Scripting Engine
- Timing and Performance
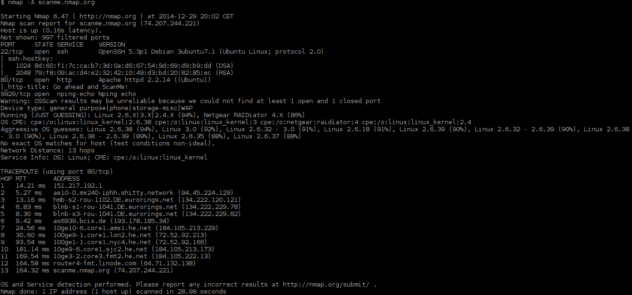
5. Real-World Examples with Pictures
Example 1: Basic TCP Connect Scan
Include a step-by-step example of performing a TCP Connect Scan on a target IP address, highlighting the command used and the resulting output.
Example 2: SYN Scan with OS Detection
Provide a detailed example of conducting a SYN Scan with OS detection, showcasing the Nmap command and explaining the significance of the results obtained.
Example 3: Service and Version Detection
Demonstrate how to use Nmap to identify services and versions running on open ports, presenting a sample command and the corresponding output.
6. Best Practices and Security Considerations
- Always ensure you have proper authorization and permission before scanning any network or system.
- Familiarize yourself with Nmap’s options and features to maximize its effectiveness.
- Regularly update Nmap to benefit from the latest bug fixes and enhancements.
- Be mindful of the potential impact of scanning on target systems, especially in production environments.
Conclusion
Nmap is an indispensable tool for network scanning and security assessments. Its versatility, combined with its extensive feature set, makes it a go-to choice for professionals seeking to understand their networks


